Untagged AWS resources are invisible in your cost reports—and invisible costs become unmanageable costs. Organizations waste 30-50% on cloud infrastructure due to poorly governed tagging, leaving FinOps teams chasing down mystery expenses instead of optimizing spend. When your engineering teams launch hundreds of resources weekly across development, staging, and production environments without consistent metadata, you end up with fragmented cost reports where the same dimension appears under seven different variations and entire categories of spend labeled simply as “unallocated.”
Automated tagging enforcement transforms AWS cost allocation from reactive guesswork into proactive, centralized governance. By combining AWS Organizations, tag policies, Service Control Policies (SCPs), and AWS Config, you ensure every resource carries the metadata necessary for accurate cost attribution before it incurs a single dollar of spend. This shift from detection to prevention is what separates organizations that understand their cloud costs from those drowning in opacity.
Why manual tagging governance fails at enterprise scale
Manual tagging strategies collapse under the weight of distributed teams, multi-account architectures, and rapid deployment cycles. Your engineering teams launch hundreds of resources weekly, and without automated enforcement, you face predictable failures. Inconsistent tag schemas emerge when development teams use “CostCenter” while marketing uses “costcenter”—AWS treats these as separate dimensions due to case sensitivity, fragmenting your cost reports and making accurate allocation impossible.
Untagged resource sprawl is inevitable when resources launched through quick CLI commands, third-party tools, or emergency incidents bypass tagging workflows entirely. These orphaned resources appear as “unallocated” in Cost Explorer, obscuring which teams or projects are actually driving your AWS bill. By the time you discover untagged resources in your monthly cost review, you’ve already paid for 30 days of invisible spend.
Reactive detection cycles mean AWS Config rules identify compliance gaps after the fact—useful for reporting, but not for prevention. Even well-tagged resources experience drift over time as teams modify tags manually or automation scripts update some attributes but not others. Your tagging taxonomy degrades month over month without active governance, and the cost allocation insights you initially gained slowly erode until they’re meaningless.
Automated enforcement addresses these failures by implementing preventive controls at the organization level. Resources that don’t meet your tagging standards simply cannot be created, shifting the burden from reactive detection to proactive prevention. This architectural change is what makes enterprise-scale tagging governance actually work.
The AWS tagging governance architecture
Effective automated tagging requires a layered architecture that combines multiple AWS services working in concert. Each layer serves a distinct role in your governance model, and understanding these roles helps you design enforcement that’s both rigorous and pragmatic.
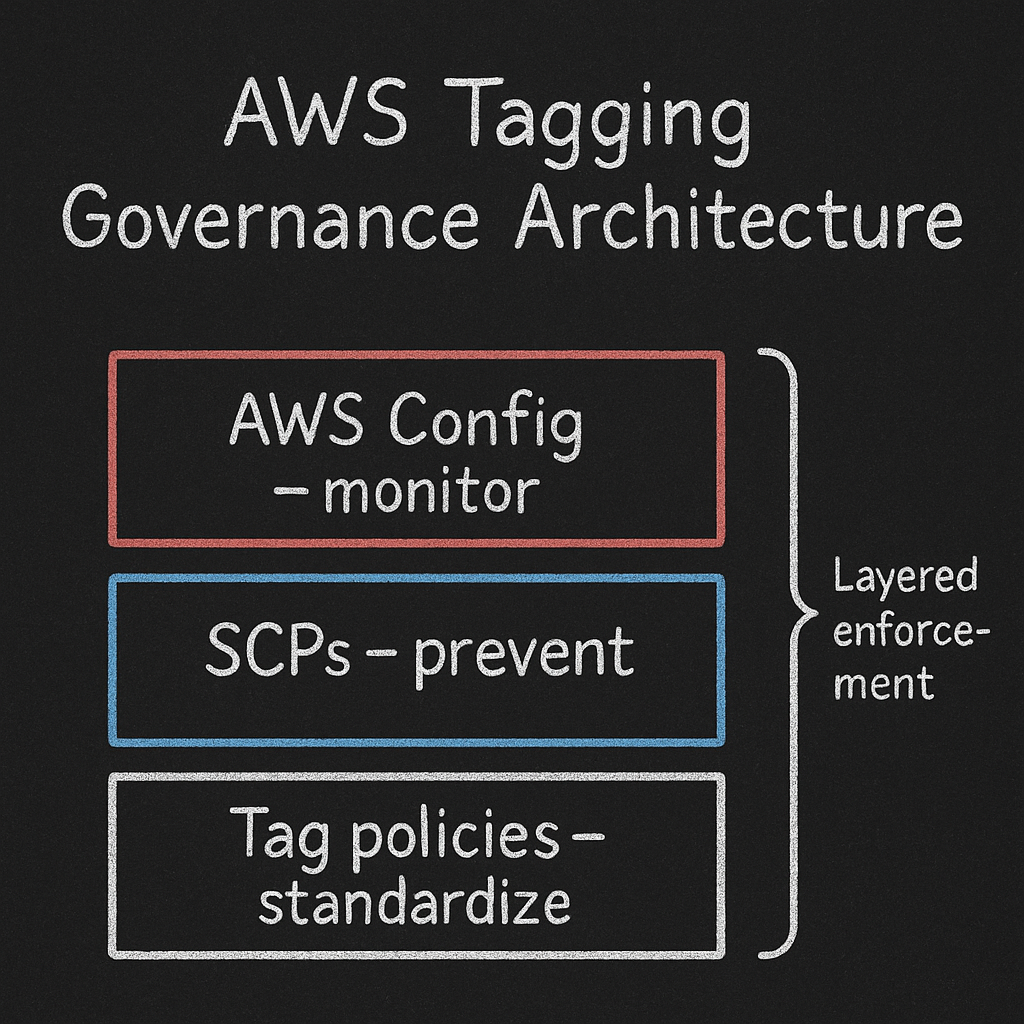
Tag policies: Standardizing metadata across your organization
Tag policies standardize tags across AWS Organization resources and define acceptable values for each tag key. Think of tag policies as your tagging data dictionary—you define that “Environment” must be one of “Production,” “Staging,” “Development,” or “Sandbox,” not the seven variations your teams might invent organically. Tag policies support case-sensitive enforcement, preventing the “CostCenter” versus “costcenter” fragmentation that breaks cost allocation reports.
When you select the “prevent non-compliant operations” option, tag policies enable preventive enforcement for specific resource types. AWS blocks resource creation if required tags are missing or contain invalid values. This enforcement currently applies to a subset of AWS services—primarily compute, storage, and database resources where cost allocation matters most. Unlike Service Control Policies, tag policies don’t deny API calls directly; instead, they establish the compliance baseline that other enforcement mechanisms reference.
The tag policy workflow starts with defining required tags in a JSON policy document—typically core allocation dimensions like CostCenter, Project, Owner, and Environment. You specify acceptable values for each tag key, attach the policy to organizational units or individual accounts, and enable enforcement mode for supported resource types. AWS recommends starting small with simple policies attached to test accounts before rolling out organization-wide enforcement. Begin with a minimal effective taxonomy of four to six mandatory tags that address your core cost allocation needs, then expand as your FinOps practice matures.
Service Control Policies: Preventive enforcement at the API layer
Service Control Policies manage permissions across your AWS Organization and provide the most powerful enforcement mechanism for tagging compliance. SCPs can deny resource creation when required tags are missing from the API request, creating a hard enforcement boundary that teams cannot bypass. This is an AWS-recommended best practice for resource tagging enforcement, particularly when implementing attribute-based access control.
An SCP-based tagging enforcement policy prevents anyone from launching EC2 instances, creating EBS volumes, or provisioning RDS databases unless they include valid CostCenter and Environment tags in the creation request. The API call fails immediately with a clear error message identifying the missing or invalid tags. This immediate feedback loop teaches teams the tagging requirements through practical experience rather than documentation they might never read.
SCPs excel at enforcing request-time tags—metadata included in the initial resource creation API call. However, not all AWS services support request tags in the same way. EC2 instances, for example, don’t support request tags validation, requiring resource tags checks instead for proper enforcement. This quirk requires different enforcement patterns for different service families, and you need to understand these limitations when designing your governance architecture.
For attribute-based access control to function reliably, you must also restrict who can modify tags after creation. SCPs can limit tag modifications to only authorized principals—typically your FinOps team or automation service accounts. This prevents well-intentioned or malicious engineers from modifying cost allocation tags after resources are deployed, ensuring tag integrity throughout the resource lifecycle. Without this restriction, teams could bypass your tagging governance by creating resources with compliant tags and then immediately removing them.
AWS Config: Continuous compliance monitoring and remediation
While tag policies and SCPs provide preventive controls, AWS Config offers continuous detection and automated remediation for tagging compliance. AWS Config evaluates resources against rules you define, flags non-compliant resources, and triggers Lambda functions to correct violations automatically. This detection layer catches resources that slip through preventive controls due to service limitations or edge cases in your enforcement logic.
The required-tags managed Config rule checks whether your resources carry specific tags. Configure it to evaluate EC2 instances, EBS volumes, S3 buckets, and other cost-significant resource types. When Config detects non-compliant resources, it can automatically invoke remediation actions through Lambda functions that apply default tags based on the resource’s account, OU membership, or CloudFormation stack metadata. For resources that should never be untagged, Lambda can terminate them or move them to a quarantine state pending manual review.
Config Rules shine in multi-account environments where you need unified compliance visibility. The Config Aggregator consolidates compliance data from all accounts in your organization, giving your FinOps team a single pane of glass for tagging health. You can quickly identify which accounts or teams have the worst tagging compliance and target education or automation improvements accordingly. This centralized visibility is what enables you to manage tagging governance across hundreds of accounts without drowning in per-account configuration.
Continuous compliance monitoring catches drift over time. As teams modify resources or automation scripts evolve, Config continuously re-evaluates tagging compliance and flags new violations within minutes—a stark improvement over monthly manual audits that only discover problems after they’ve been accumulating for weeks.
Implementing automated tagging: A phased rollout approach
Deploying automated tagging governance requires careful planning to avoid disrupting existing workloads while building the foundation for accurate cost allocation. A phased approach balances enforcement rigor with operational reality, giving teams time to adapt while progressively tightening controls.
Phase 1: Baseline and educate
Start by understanding your current tagging state. Use AWS Resource Groups Tagging API or third-party tools to generate a comprehensive inventory of your resources and their existing tags. This baseline reveals your starting point and helps you prioritize enforcement efforts—if only 20% of your EC2 instances carry cost allocation tags, you know tagging discipline is weak and need stronger preventive controls.
Document your tagging taxonomy and publish it to all engineering teams. AWS recommends deciding on a consistent capitalization strategy upfront—either CamelCase (CostCenter) or lowercase (costcenter)—because AWS treats these as different tag keys. Pick one standard and document it clearly. Your taxonomy should define required tags (typically four to six core allocation dimensions), optional tags that teams may add for their own purposes, acceptable values for each tag key (closed list whenever possible), and tag naming conventions (no spaces, use hyphens, maximum length).
Educate account administrators on the tagging strategy. Untagged resources don’t appear as noncompliant in tag policy compliance reports—only resources with incorrect tag values show up. Teams need to understand that “no tag” and “wrong tag” are both failures, even if compliance dashboards don’t always surface the former. This education phase prevents the confusion and resistance that derails many governance initiatives.
Phase 2: Deploy detection and monitoring
Before enforcing preventive controls, deploy detection mechanisms to understand what would break. Create AWS Config rules for required tags across all resource types in a non-enforcing mode. Monitor compliance reports for two weeks to see how many resources would fail enforcement if you activated it today, which teams or accounts have the worst compliance, and what resource types are most commonly untagged.
Deploy tag policies in audit-only mode attached to test accounts or non-critical organizational units. Tag policies generate compliance reports showing which resources violate your standards without blocking their creation. Review these reports to refine your taxonomy before full enforcement—you may discover that certain tag values you defined aren’t actually used by any teams or that teams need additional acceptable values you hadn’t anticipated.
Set up CloudWatch dashboards and SNS alerts for tagging compliance metrics. Track the percentage of resources with required tags, number of non-compliant resources per account, trend of compliance over time, and top violating teams or services. This visibility helps you communicate progress to leadership and hold teams accountable as you move toward preventive enforcement.
Phase 3: Enable preventive controls incrementally
Start enforcing tagging requirements in non-production environments first. Activate tag policy enforcement mode for development and staging accounts where resource creation failures cause minimal business impact. Teams learn the new requirements through immediate feedback when their untagged resource creation attempts fail, and this practical education is far more effective than documentation alone.
Create Service Control Policies that deny resource creation without required tags, again starting with non-production OUs. The SCP should return clear error messages that explain which tags are missing and what values are acceptable—a good error message accelerates adoption by eliminating the investigation overhead that would otherwise slow teams down.
Monitor support tickets and Slack channels for friction points. Address issues quickly with documentation, automation improvements, or temporary exceptions. After two to three weeks of successful enforcement in non-production, extend preventive controls to production environments. Schedule the rollout during a maintenance window and communicate it broadly. Production enforcement inevitably surfaces edge cases—emergency incident response procedures, disaster recovery automation, or vendor-provided CloudFormation templates that don’t support tagging—and you need processes to grant temporary exceptions while you build proper solutions.
Phase 4: Automate remediation and optimize
With preventive controls in place, shift focus to automated remediation of existing untagged resources and continuous optimization of your tagging strategy. Deploy Lambda functions triggered by Config Rules that apply default tags to untagged resources based on context (account, OU, stack), propagate tags from parent resources to children (EC2 to EBS volumes, RDS to snapshots), and notify resource owners when their resources are auto-tagged with defaults.
Integrate tagging enforcement into your infrastructure-as-code workflows. CloudFormation and Terraform should include required tags in all resource definitions, ideally using variables that reference a central taxonomy definition. This shift-left approach catches tagging issues during code review rather than at deployment time, preventing compliance violations before they enter production.
Continuously refine your taxonomy based on cost allocation needs. As your cost visibility improves, you may identify new dimensions for analysis or discover that certain tags you enforced aren’t actually used in reporting. Prune unused tags to reduce cognitive overhead while adding new ones that unlock better optimization opportunities.
Advanced enforcement patterns for complex environments
Standard tag policies and SCPs handle most tagging enforcement needs, but complex multi-account organizations require advanced patterns to address edge cases and special requirements that emerge at enterprise scale.
Conditional enforcement based on resource characteristics
Not all resources require the same tagging rigor. Apply stricter enforcement to production resources while allowing more flexibility in sandbox accounts. An SCP can deny production EC2 instance creation unless the CostCenter tag is present, but allow untagged instances in other environments. Production resources typically represent 60-80% of your AWS spend, so enforcing strict tagging there captures the majority of your cost allocation needs while giving development teams more freedom to experiment.
This conditional approach recognizes that perfect tagging compliance isn’t always worth the operational friction. Development environments turn over rapidly—resources created for a two-hour test and then terminated—and requiring full tagging rigor on these ephemeral resources adds overhead without proportional benefit. Focus your strictest enforcement on the resources that matter most to cost allocation.
Automated tag propagation from management layers
Enforce tagging at the account or OU level, then automatically propagate those tags to resources created within that scope. Use Lambda triggered by CloudWatch Events to apply account-level tags to all new resources. This pattern works well for business unit segregation where entire accounts belong to specific cost centers—engineers don’t need to remember the CostCenter tag because it’s automatically inherited from account metadata.
Tag propagation reduces the tagging burden on engineering teams while maintaining compliance. Rather than asking every developer to correctly tag every resource they create, you establish organizational metadata once at the account level and let automation handle the details. This approach is particularly valuable for teams that primarily interact with AWS through the console rather than infrastructure-as-code where tag templates are easier to maintain.
Service-specific enforcement for tagging limitations
Different AWS services handle tags differently, requiring service-specific enforcement logic. EC2 instances don’t support request-time tag validation, so you must check tags on the resource after creation using resource tag conditions rather than request tag conditions. This subtle difference in SCP syntax trips up many organizations implementing tagging governance for the first time.
For services that don’t support tag-based SCPs at all, use Config Rules with automated termination. A Lambda function evaluates new resources against your tagging policy and terminates those that don’t comply within a grace period—typically one hour. The grace period gives teams time to add tags to resources they just launched, preventing false positives from brief timing windows. This aggressive enforcement approach works well for environments where untagged resources should never exist, but requires clear communication so teams understand the automatic cleanup behavior.
Integrating automated tagging with AWS Cost Explorer and billing workflows
Automated tagging enforcement only delivers value when you activate those tags in AWS Cost Explorer and build reporting workflows that leverage them. Without this final step, you’ve invested in governance infrastructure that doesn’t impact your actual cost allocation.
Activating cost allocation tags
Every tag you want to use in Cost Explorer must be explicitly activated in the AWS Billing and Cost Management console. Navigate to Cost Allocation Tags and activate both AWS-generated tags (aws:createdBy, aws:cloudformation:stack-name) and your user-defined tags (CostCenter, Project, Environment, Owner). This commonly overlooked step is what actually makes your tags appear in cost reports—enforcement ensures tags exist on resources, but activation makes them visible to billing systems.
Activated tags typically take 24 hours to appear in your cost reports and only apply to costs incurred after activation. Historical costs remain untagged even if you retroactively apply tags to old resources. This lag means you should activate cost allocation tags as soon as you define your taxonomy—long before you enforce them—to minimize the gap in your cost visibility. Organizations that wait to activate until after full enforcement rollout lose months of tagged cost data unnecessarily.
Building tag-based cost allocation reports
With tags activated, Cost Explorer enables powerful cost allocation analysis. Create saved reports that group costs by your primary allocation dimensions. A department chargeback report groups by CostCenter tag, filters to Production environment, and displays monthly trends—this report becomes your monthly invoice to each business unit, showing exactly what they consumed.
Project profitability analysis groups by Project tag, includes all environments, and compares actual spend to project budgets. This reveals which initiatives are over-budget and need cost optimization attention. Environment distribution reports group by Environment tag across all cost centers—typical healthy ratios show production as 60-70% of spend with development and staging splitting the remainder, and deviations from this pattern indicate opportunities for environment scheduling or rightsizing.
These reports transform from manual monthly exercises into automated dashboards that update daily, giving stakeholders real-time visibility into their cloud consumption. The shift from retrospective analysis to continuous monitoring changes how teams think about cloud costs—instead of discovering problems weeks later, they see trends as they develop.
Tag-based AWS Budgets and anomaly detection
Create AWS Budgets scoped to specific tag values to delegate budget ownership to teams. A marketing team with CostCenter=Marketing gets their own budget that alerts them at 80% utilization—they don’t need to parse organization-wide cost reports to find their spend. This delegation transforms cost management from a centralized FinOps function into a distributed responsibility where teams own their consumption.
Configure Cost Anomaly Detection monitors filtered by tags to catch unusual spend patterns in specific projects or environments. When the Development environment suddenly spikes by 200%, you get an immediate alert rather than discovering it in next month’s bill. Learn more about effective anomaly detection strategies. This enables rapid response—often within hours rather than weeks—and the difference between catching an anomaly the same day versus the same month can mean thousands of dollars in prevented waste.
Tag-based budgets and anomaly detection shift cost awareness from centralized FinOps teams to distributed engineering teams. When developers receive direct alerts that their project is over budget, they take ownership of optimization rather than treating it as someone else’s problem. This cultural shift is often more valuable than the technical automation itself.
Chargeback and showback workflows
For organizations practicing chargeback (billing departments for their actual usage) or showback (reporting costs without transferring budgets), automated tagging enables accurate attribution. Export your Cost and Usage Report filtered by cost allocation tags and feed it into your financial systems. The granularity of tag-based allocation means you can confidently allocate 90%+ of your cloud spend to specific cost centers, projects, or initiatives rather than spreading costs across the organization using crude approximations.
Showback works particularly well for teams just starting FinOps practices. Rather than immediately implementing hard budgets, show teams their allocated costs monthly and ask them to identify optimization opportunities. As tagging discipline improves and teams become comfortable with their cost visibility, transition to chargeback models with real budget transfers. This gradual progression builds FinOps maturity without triggering organizational resistance to sudden budget accountability.
Optimizing AWS costs through tag-driven automation
Accurate tagging doesn’t just enable cost allocation—it unlocks automated optimization that can significantly reduce your AWS bill. Once resources carry metadata describing their purpose, ownership, and criticality, you can apply automated cost optimization techniques selectively and safely.
Intelligent scheduling based on environment tags
Development and staging environments rarely need to run 24/7. Use Environment tags to automatically schedule start/stop routines that reduce runtime from 168 hours per week to 40 hours—a 76% reduction in compute costs for non-production resources. An AWS Lambda function triggered by CloudWatch Events evaluates Environment tags and applies instance schedulers that stop instances outside business hours (weekdays 8am-6pm). This pattern alone commonly recovers 20-30% of total EC2 costs in organizations with large development footprints, and the Environment tag provides the signal for safe automation—you’d never want to apply this logic to production resources.
The key insight here is that tags transform generic cost optimization recommendations into contextualized actions. Without the Environment tag, you have no way to distinguish production instances that must run continuously from development instances that can safely shut down overnight. The tag provides the business context that makes automation both safe and effective.
Lifecycle policies driven by classification tags
Storage costs accumulate invisibly as teams generate snapshots, backups, and logs without cleanup policies. Use tags to apply appropriate lifecycle management—an S3 lifecycle policy can automatically archive non-critical data to Glacier after 30 days and delete it after 90 days, but only when explicitly tagged as safe to do so. Without the DataClassification tag, objects follow default retention policies that prioritize data preservation over cost efficiency.
This selective automation prevents the two failure modes that plague storage optimization: either you’re too aggressive and delete data someone needed, or you’re too conservative and accumulate endless storage costs. Tags let you tune lifecycle policies to the actual business value of each dataset rather than applying one-size-fits-all rules.
Reserved Instance and Savings Plan allocation
Tag-driven cost allocation reveals which projects or teams consume consistent baseline capacity—the ideal candidates for Reserved Instances or Savings Plans. Use your Cost Explorer reports grouped by Project tag to identify workloads with steady utilization patterns over 60+ days. Rather than purchasing organization-wide commitments based on aggregate usage, allocate Reserved Instances to specific projects using tag-based attribution.
When a Reserved Instance provides a discount, Cost Explorer shows which tagged resources benefited. This enables accurate chargeback that reflects both usage-based costs and commitment-based savings. For teams experimenting with new projects, defer commitment purchases until their tagging data shows stable utilization patterns—you avoid premature RI purchases for projects that might pivot or scale down within the commitment period. Explore more about intelligent forecasting to support commitment decisions.
Automated rightsizing workflows
Combine tagging with utilization metrics to identify rightsizing opportunities safely. Automated cost visibility platforms ingest CloudWatch metrics alongside tag metadata to recommend instance type changes that preserve performance while reducing cost. When an EC2 instance tagged Project=Website-Backend and Environment=Production shows consistent 15% CPU utilization over 30 days, automation can safely recommend downgrading from m5.2xlarge to m5.large.
The tags provide business context—this is production infrastructure for a specific project—enabling informed decisions about change windows and rollback procedures. Without tags, rightsizing tools produce generic recommendations that lack business context, and engineers waste time investigating “which workload runs on i-abc123def456” before they can evaluate whether a change is safe. Tags eliminate this investigation overhead and accelerate optimization implementation.
Common pitfalls and how to avoid them
Organizations implementing automated tagging governance consistently encounter the same failure patterns. Anticipate these issues and build solutions into your deployment plan to avoid months of wasted effort.
Over-engineering the tag taxonomy upfront
The temptation to define a perfect taxonomy with 20+ required tags creates compliance paralysis. Teams can’t remember the acceptable values for Environment, Application, Tier, Component, Function, DataClassification, ComplianceScope, and ten other dimensions. They work around your enforcement using placeholder values or delay deployments while debating which tag values apply. AWS recommends starting with four to six mandatory tags that address your immediate cost allocation needs—add new required tags only when you have specific use cases and stakeholder demand.
Your taxonomy should grow organically based on actual reporting needs, not theoretical future requirements. Start with the minimum viable taxonomy that enables basic cost allocation, then expand incrementally as you discover new optimization opportunities or chargeback requirements. This approach builds FinOps maturity gradually rather than demanding perfection immediately.
Enforcing tags before activating them in billing
Teams sometimes deploy tag policies and SCPs months before activating the tags in Cost Allocation Tags. This creates a gap where resources are properly tagged but those tags don’t appear in Cost Explorer or CUR—defeating the entire purpose of tagging governance. Activate cost allocation tags immediately when you define your taxonomy, even before you enforce them. The 24-hour activation delay means you’ll start collecting tagged cost data right away, and by the time you roll out enforcement several weeks later, you already have historical data showing cost allocation by tag.
This timing is counterintuitive because enforcement feels more urgent than activation, but the activation step is what actually makes tags valuable for cost management. Without activation, you’ve built compliance infrastructure that doesn’t impact your actual cost visibility.
Insufficient error messaging in denial policies
When an SCP denies resource creation due to missing tags, a generic “Access Denied” error frustrates engineers and generates support tickets. They don’t understand which tag is missing or what values are acceptable. While SCPs don’t support custom error messages directly, the policy structure itself communicates the requirement. Supplement this with documentation that links to your tagging standards and examples of correct API calls.
Consider implementing a Slack bot or internal documentation site that engineers can query when they encounter tagging denials. The bot can parse the SCP that was violated and return specific guidance about which tags to add and what values are acceptable. This self-service approach prevents enforcement from becoming a bottleneck that slows deployment velocity.
Forgetting to tag automation service accounts
Your Lambda functions, Systems Manager automation documents, and CloudFormation deployments need permission to create resources—but they also need to include required tags. If your SCP denies untagged EC2 instance creation, your auto-scaling automation breaks unless it includes tags in the RunInstances call. Build tag parameters into all automation scripts and grant your service accounts permission to use specific tag values.
An automation service account might default to CostCenter=Automation and Environment=Production so all automated resource creation complies with your tagging policy. This requires coordination between your FinOps team defining tagging requirements and your platform engineering team building automation—another reason why successful tagging governance is as much organizational as technical.
Ignoring inherited AWS-generated tags
AWS automatically generates tags for resources created through certain services: aws:cloudformation:stack-name, aws:cloudformation:logical-id, aws:autoscaling:groupName. These tags provide valuable context for cost allocation without any manual effort. Activate AWS-generated cost allocation tags alongside your user-defined tags—when resources are deployed via CloudFormation, the stack name becomes a cost allocation dimension, often correlating to projects or applications.
This gives you basic cost attribution even for resources that lack user-defined tags, reducing the impact of compliance gaps during your enforcement rollout. Think of AWS-generated tags as your safety net—they won’t provide perfect allocation, but they’re better than nothing when teams forget user-defined tags.
Measuring success: KPIs for tagging governance
Track quantitative metrics that demonstrate the business value of your automated tagging investment and help you identify where additional enforcement or education is needed.
Tag compliance rate measures the percentage of resources with all required tags. Target 95%+ compliance after your initial rollout phase—compliance below 90% indicates insufficient enforcement or too many exceptions. Track this metric by account and resource type to identify specific areas needing attention.
Cost allocation coverage shows the percentage of total AWS spend that carries cost allocation tags and can be attributed to specific teams or projects. Organizations with mature tagging practices achieve 90%+ coverage, meaning less than 10% of spend appears as “unallocated” in reports. This metric directly measures whether your tagging governance is achieving its primary goal of enabling accurate cost attribution.
Time to cost attribution tracks how long it takes to answer “who owns this expensive resource?” In the past, this required CloudTrail analysis, interviewing teams, and detective work—often taking days. With proper tagging, you get instant answers by filtering Cost Explorer. Measure this by timing how long it takes to attribute ownership for a sample of high-cost resources each month.
Chargeback accuracy measures the percentage of monthly cloud costs that can be confidently allocated to specific cost centers for organizations practicing chargeback. Anything below 85% suggests tagging gaps that require enforcement improvements. Compare allocated costs to actual invoices to ensure your chargeback reflects reality.
Optimization opportunity identification rate counts how many cost optimization projects are enabled by tag-driven analysis—examples include scheduling non-production environments, rightsizing specific applications, or eliminating orphaned resources. Strong tagging governance should enable five to ten new optimization initiatives per quarter, and this metric measures whether your tagging investment is unlocking actual savings.
Exception request volume tracks requests for tagging policy exceptions or temporary exemptions. High exception volume (more than ten requests per month) suggests your taxonomy is too rigid or your enforcement is blocking legitimate use cases. Low exception volume indicates teams have internalized the tagging requirements and aren’t fighting your governance model.
Building a comprehensive AWS cost governance framework
Automated tagging is the foundation of AWS cost allocation strategies, but it works best as part of a broader cost governance framework. Layer additional controls on top of your tagging infrastructure to create defense in depth.
AWS Budgets with tag-based scoping creates budgets for each cost center using CostCenter tag filters. When Marketing exceeds 80% of their monthly budget, alert the marketing director directly rather than the central FinOps team. This delegates budget ownership and makes cost management a distributed responsibility rather than a centralized function.
Service Quotas aligned to cost policies limit expensive resource types in development accounts. Even if a developer tags resources correctly, they can’t accidentally launch 100 GPU instances if the account quota is set to five. This prevents both honest mistakes and runaway automation from generating massive unexpected bills.
AWS Cost Anomaly Detection filtered by tags configures separate anomaly detection monitors for production and non-production environments. A 200% cost spike in development is less urgent than a 30% spike in production, and tag-filtered monitoring enables appropriate alerting. You avoid alert fatigue from development experiments while maintaining tight monitoring of production costs.
Automated policy-as-code reviews store your tag policies, SCPs, and Config rules in version control and require pull requests and FinOps review for any changes to enforcement policies. This prevents ad-hoc exceptions that degrade compliance over time—every relaxation of enforcement goes through a formal review process where you evaluate the trade-offs.
Regular tagging audits and refinement schedules quarterly reviews of your tagging taxonomy with stakeholders from finance, engineering, and product teams. Add tags that enable new insights, deprecate unused tags that add compliance overhead, and adjust acceptable values as your organization evolves. This ensures your tagging strategy remains aligned with business needs rather than ossifying into a bureaucratic obstacle.
This layered approach ensures that tagging governance integrates with your broader FinOps practices rather than existing as an isolated initiative. The goal isn’t perfect tagging compliance—it’s actionable cost visibility that drives optimization decisions and enables your organization to manage cloud spend effectively.
Accelerating AWS cost optimization with automation
Organizations that implement robust tagging governance typically uncover substantial savings opportunities through the insights enabled by accurate cost allocation. You identify which projects consume the most resources, which teams have the worst cost efficiency, and which environments offer the greatest optimization potential. Understanding the role of tagging in effective cloud cost management is the first step toward realizing these savings.
However, identifying savings opportunities doesn’t automatically realize those savings. The gap between visibility and action is where most FinOps initiatives stall. Your team generates reports showing 500 underutilized instances, 200 orphaned EBS volumes, and dozens of rightsizing opportunities—but implementing these changes requires engineering time that your team doesn’t have. Manual optimization at this scale is simply not feasible, and the savings opportunities you identify through tagging remain theoretical rather than actual.
This is where specialized automation platforms deliver value by bridging the gap from cost visibility to automated optimization. While your tag-based reports show which resources are candidates for scheduling, rightsizing, or Reserved Instance coverage, automation platforms safely execute those changes—validating performance impact and rolling back if necessary. Automated platforms also continuously manage the optimization opportunities that tagging reveals, adapting strategies in real-time as your environment evolves rather than waiting for quarterly FinOps reviews.
The result is a complete cost governance loop: tagging provides attribution and visibility, analysis identifies opportunities, automation implements changes, and monitoring validates results. Each component strengthens the others, creating a system that continuously optimizes your AWS spend without requiring constant manual intervention.
Transform tagging governance into measurable savings
Automated tagging governance gives you the visibility to understand your AWS costs, but visibility alone doesn’t reduce your bill. You need the combination of accurate cost allocation through tagging and automated optimization to actually capture the 30-40% savings hiding in your environment.
Hykell specializes in automating the entire optimization workflow—from identifying opportunities through your tag-based cost allocation to safely implementing changes across your AWS environment. We only charge based on actual savings delivered, which means if you don’t save, you don’t pay. This performance-based model aligns our incentives with yours: we succeed when you reduce costs, not when we sell more software licenses.
Start by getting visibility into what your automated tagging could unlock. Visit the Hykell knowledge base to explore more strategies for AWS cost optimization, or contact our team to analyze your specific environment and identify your savings potential. Most organizations discover that the combination of proper tagging governance and automated optimization delivers results far beyond what either approach could achieve independently.