Are you paying more to move your data than to process it? NAT Gateway charges frequently rank as a top-three expense for high-traffic AWS environments, yet they are often overlooked. Here is how to diagnose these hidden drivers and re-architect your VPC for significant savings.
Decoding the NAT Gateway invoice: the three cost layers
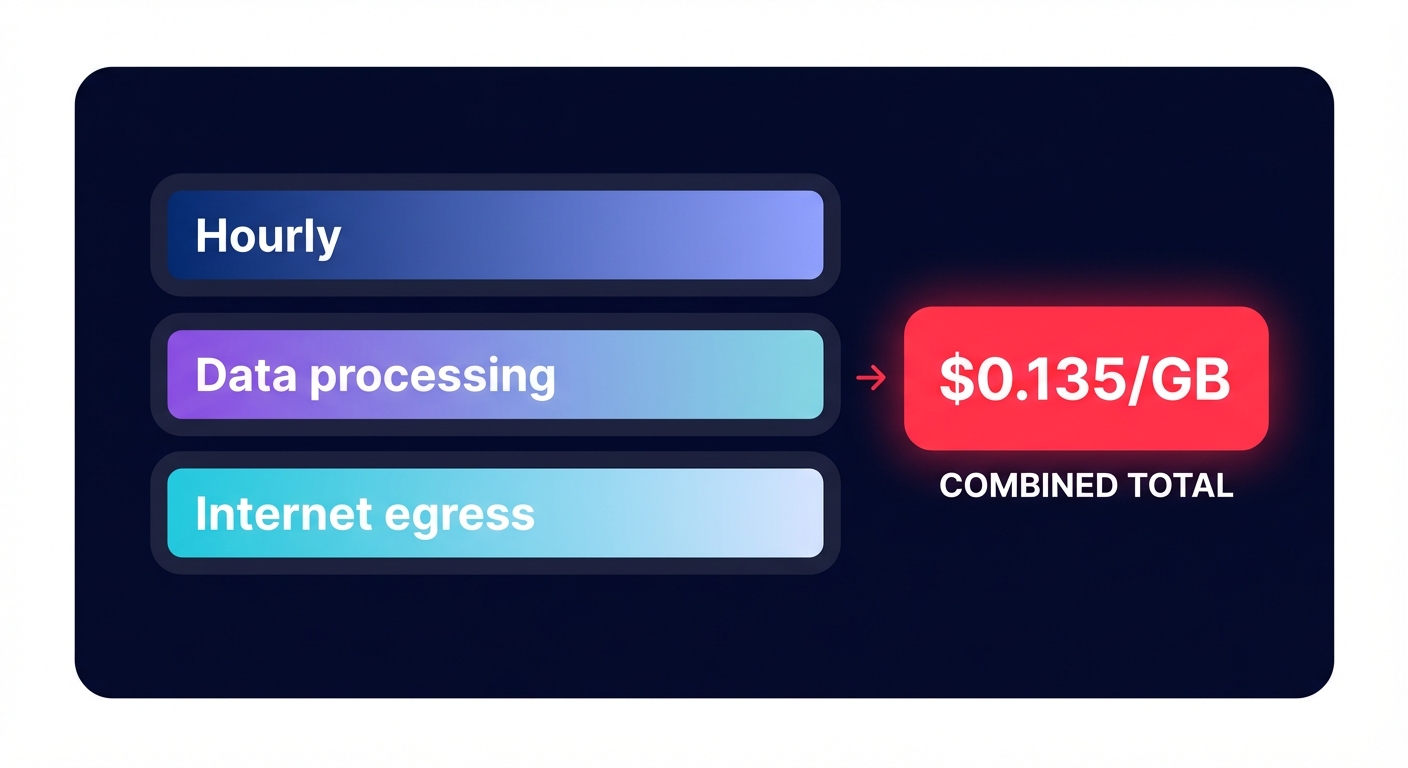
To reduce your spend, you must first understand the three distinct ways AWS bills you for every NAT Gateway in your VPC. In many US regions, the baseline starts with an hourly uptime charge of $0.045 per gateway. If you follow high-availability best practices and deploy one in each of the three Availability Zones (AZs), you are paying nearly $100 per month before a single byte of data even moves.
The real silent killer is the data processing fee. AWS charges $0.045 per GB for all data passing through the gateway. This applies regardless of where the data is going – even if it is staying within the AWS network to reach services like S3 or Amazon ECR. Finally, if that data is bound for the public internet, you are hit with standard AWS egress costs of approximately $0.09 per GB.
When you combine these layers, your internet-bound traffic costs a staggering $0.135 per GB. To put this in perspective, pulling 178,000 GB of container images from ECR through a NAT Gateway can result in $8,010 per month in processing fees alone. These costs scale linearly with your traffic, meaning a simple misconfiguration can cause your bill to balloon overnight.
How to diagnose your hidden traffic drivers
Before you can re-architect your network, you need to know which resources are burning your budget. You should start by using AWS Cost Explorer and filtering by the “EC2-Other” category to isolate specific NAT Gateway resource charges. If you see a massive spike in “NATGateway-Bytes,” you likely have a high-volume data mover residing in a private subnet.
For more granular insights, you should implement the following diagnostic steps:
- Analyze VPC Flow Logs using CloudWatch Logs Insights to query which internal IP addresses are sending the most traffic to your NAT Gateway’s elastic IP.
- Enable and enforce AWS cost allocation tags to see which specific projects, environments, or teams are driving throughput.
- Monitor your environment with AWS network performance monitoring to distinguish between application-level issues and underlying infrastructure bottlenecks.
- Set up AWS Cost Anomaly Detection to receive real-time alerts the moment a misconfigured log export or an oversized container image pull causes a spend deviation.
Architecture patterns to bypass NAT Gateway fees
The most effective way to reduce NAT costs is to stop using the gateway for traffic that never needs to leave the AWS global network. AWS provides two types of VPC endpoints that allow your private instances to communicate with AWS services privately and more affordably.
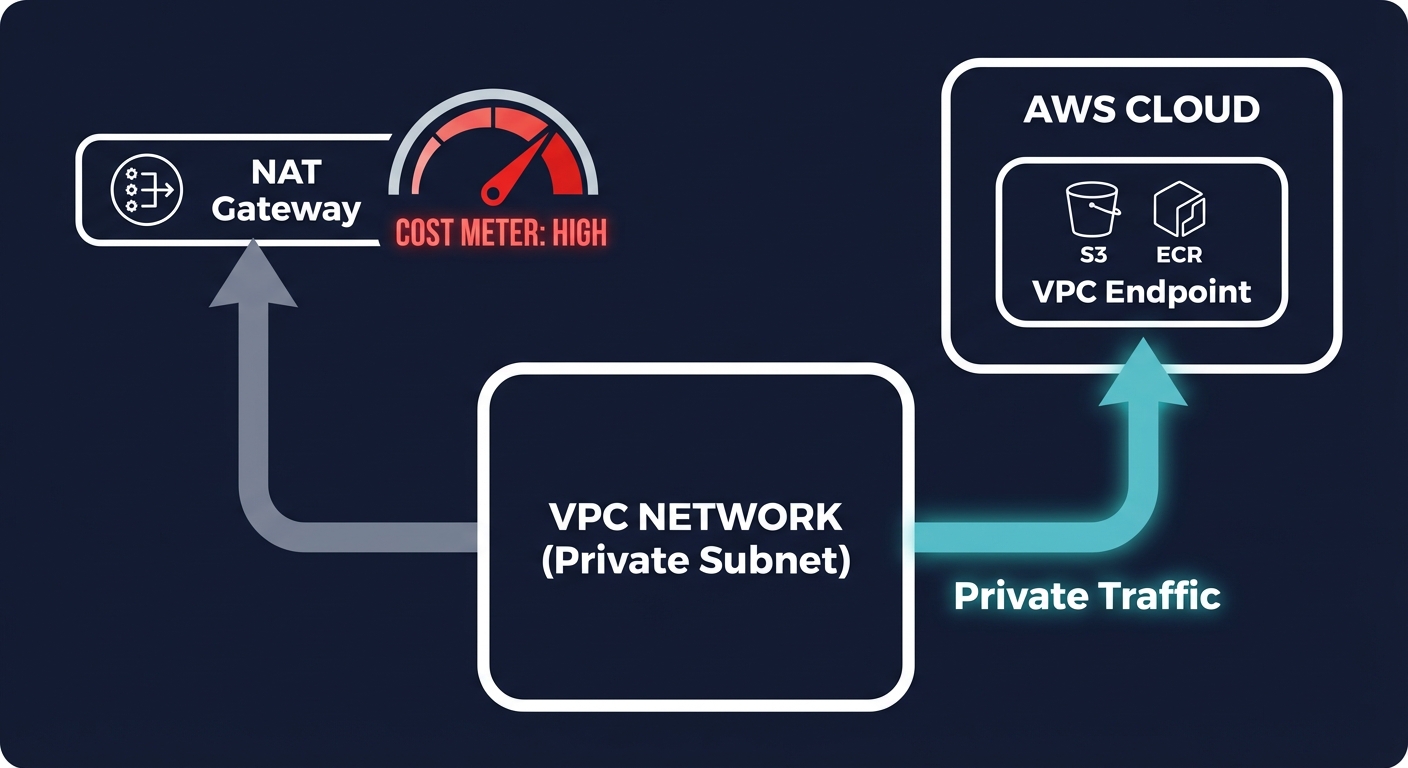
Gateway endpoints for S3 and DynamoDB
Gateway endpoints for S3 and DynamoDB are completely free. They incur zero hourly charges and zero data processing fees. By simply adding a Gateway endpoint to your VPC route table, you eliminate the $0.045/GB processing fee for all your storage traffic. For a workload moving 10 TB of data to S3 monthly, this single configuration change saves you $450 every month.
Interface endpoints for ECR and Secrets Manager
For services like Amazon ECR, Kinesis, or Secrets Manager, you must use interface endpoints powered by AWS PrivateLink. While these have a small hourly cost and a processing fee of roughly $0.01/GB, they are still 78% cheaper than routing that same traffic through a NAT Gateway. High-volume container workloads often see their networking costs drop by thousands of dollars after making this switch, as it replaces the heavy $0.045/GB NAT tax with a much smaller fraction.
When to centralize or decentralize your networking
Cross-AZ data transfer is another hidden tax, costing $0.01/GB for data moving between zones. If your resources in one Availability Zone are using a NAT Gateway located in a different zone, you are paying for the NAT processing plus the cross-AZ transfer fee.
If your cross-AZ traffic exceeds 4.5 GB per hour, it is actually cheaper to provision a separate NAT Gateway in every AZ. This architecture eliminates the $0.01/GB cross-zone fee, which eventually outweighs the $32 per month hourly uptime charge for the additional gateway. Conversely, for large organizations with dozens of VPCs, using a centralized egress VPC with a Shared Transit Gateway can simplify management. However, Transit Gateway adds its own $0.02/GB processing fee, so you must carefully calculate whether the reduction in total NAT Gateway hourly fees offsets the new Transit Gateway throughput costs.
Moving from manual audits to automated savings
Manually tracking every VPC endpoint and routing change is a demanding task for any engineering team. While the AWS Cost Optimization Hub provides basic recommendations, it often misses the nuanced traffic patterns that justify complex architectural shifts. Relying solely on manual reviews frequently leaves 30% or more of your networking spend on the table.
Hykell takes the guesswork out of network optimization. Our platform performs deep, automated audits of your traffic patterns to identify exactly where VPC endpoints or regional NAT Gateway adjustments will yield the highest ROI. We provide the AWS rate optimization and architectural automation needed to implement these changes safely without interrupting your services.
Because Hykell operates on a “pay-from-savings” model, you only pay a slice of the actual money we save you. If we do not find waste in your NAT Gateway configuration, you do not pay anything. You can check your potential savings today and stop letting hidden networking fees erode your cloud margins.