Can you reduce your attack surface and power consumption by 60% simultaneously? AWS Graviton instances offer inherent security advantages over x86, but the architectural shift to ARM64 requires specific hardening and compliance strategies. Mastering these nuances is essential for DevOps teams balancing performance gains with a robust security posture.
Understanding the architectural security advantage of Graviton
The security benefits of Graviton begin at the silicon level. Unlike x86 instances that rely on hyperthreading to present multiple virtual cores, AWS Graviton maps one vCPU to one physical core. This 1:1 mapping is a significant security win because it eliminates entire classes of side-channel attacks, such as Spectre and Meltdown, which exploit the shared resources of simultaneous multithreading. By removing the need for shared execution resources between vCPUs, Graviton provides a cleaner isolation boundary for your most sensitive workloads.
Hardware-level isolation and the Nitro System
Graviton is built exclusively on the AWS Nitro System, a hardware-based virtualization framework that offloads security, storage, and networking functions to dedicated hardware. This design minimizes the footprint of the traditional hypervisor, reducing the potential for compromise. The Nitro Security Chip provides a hardware root of trust, ensuring that only authenticated code is executed during the boot process. When you migrate applications to Graviton instances, you are moving to an architecture designed for modern isolation, where hardware-level encryption is the standard rather than a bolt-on feature.
Hardening the Graviton instance lifecycle
Securing your ARM-based environment requires a focus on the entire deployment lifecycle, from the initial Amazon Machine Image (AMI) to the runtime environment. Because Windows Server is not supported on Graviton, your hardening efforts will focus on Linux distributions like Amazon Linux 2023, Ubuntu, or RHEL, which have mature ARM64 support. These distributions are optimized for Graviton, ensuring that the latest security patches and kernel updates are tailored for ARM architectures.
Image management and toolchain security
When building your images, you should prioritize performance best practices for Graviton, which include using modern compilers like GCC or LLVM. These toolchains include security features like Stack Smashing Protection (SSP) and Control-Flow Integrity (CFI) specifically tuned for the ARM64 instruction set. In your CI/CD pipelines, you must manage multi-architecture support challenges carefully. Using tools like Docker buildx to create multi-arch manifests ensures your security scanners can inspect both amd64 and arm64 image layers. It is a common pitfall to assume a scan on an x86 image covers its ARM64 counterpart, as dependencies and library versions frequently differ between architectures.
Aligning ARM deployments with compliance frameworks
For organizations operating under SOC 2, HIPAA, or PCI DSS, Graviton instances fit seamlessly into existing navigating cloud performance compliance standards. AWS Nitro-based instances support always-on memory encryption, which encrypts data as it moves between the processor and the instance’s local memory to protect against physical hardware access. This capability is a core requirement for many high-security certifications and is enabled by default on modern Graviton generations.
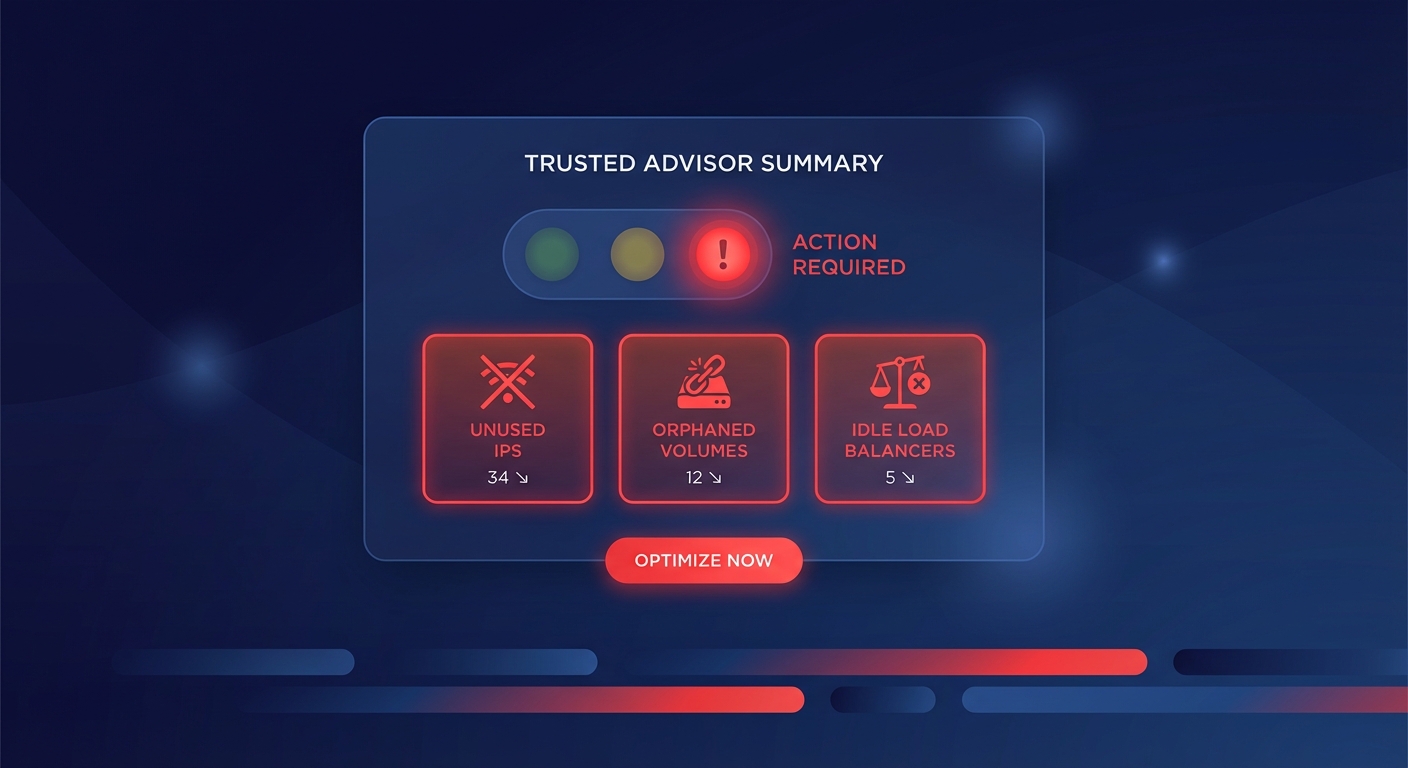
To maintain continuous auditability, you should integrate your Graviton deployments with AWS Audit Manager and AWS Config. These tools can automatically collect evidence that your ARM-based instances are utilizing encrypted EBS security best practices and are correctly tagged for data classification. Because Graviton instances are often deployed within Graviton in auto-scaling groups, ensuring that your launch templates enforce encryption by default is a critical compliance control that prevents configuration drift during rapid scaling events.
Monitoring and observability for ARM-based workloads
Effective security relies on high-fidelity monitoring, but migrating to Graviton means your performance baselines will shift. For instance, Graviton4 features DDR5-5600 memory, which provides significantly higher bandwidth than older x86 instances. What looks like normal memory traffic on an x86 workload might indicate a bottleneck or an anomaly on Graviton. You should implement AWS CloudWatch application monitoring to track these architecture-specific metrics and set appropriate alarms for utilization and latency.
If you observe a sudden drop in the percentage of Graviton instances in a mixed-architecture cluster, it could signal a compatibility issue or a configuration error in your launch templates. To manage these complex environments without increasing your operational burden, the Hykell observability platform provides real-time, role-based dashboards. These views help DevOps and security teams spot anomalies across diverse instance families before they impact the bottom line or compromise your security posture.
Automating Graviton security and cost with Hykell
Security and cost optimization are fundamentally linked, as both require total visibility and granular control over your infrastructure. Migrating to Graviton is one of the most effective ways to accelerate your Graviton gains, but managing rate optimization and right-sizing across thousands of ARM and x86 instances is an engineering challenge. Manual efforts often lead to underutilized resources or missed commitment opportunities that can erode the price-performance benefits of ARM64.
Hykell solves this by automating the heavy lifting of cloud financial management. Our platform identifies the best candidates for Graviton migration and applies AWS rate optimization strategies that stack Graviton’s 20-40% savings with Savings Plans and Reserved Instances. By operating on autopilot, Hykell ensures your infrastructure is always running on the most cost-effective and secure hardware without requiring constant manual intervention from your engineering team.
By combining the inherent security of the ARM architecture with automated optimization, you can achieve a more resilient and efficient cloud footprint. If you are ready to see how much your organization could save by moving to a secure, hardened Graviton architecture, use our cost savings calculator or book a free audit to uncover hidden inefficiencies in your AWS environment today.